🚨 Incident Response Alert Routing
Data Breach
You have identified a data breach, now what?
Your Incident Response Playbook is up to date. You have drilled for this, you know who the key players on your team are and you have their home phone numbers, mobile phone numbers, and email addresses, so you get to work. It is seven o’clock in the evening so you are sure everyone is available and ready to respond, you begin typing “that” email and making phone calls, one at a time.
Incident Response Planning
There are a number of things wrong with this scenario:
- How often do you drill and practice incident response?
- Are we lucky enough for these incidents to happen at a decent time of the day?
- How long does it take to write “that” email?
- How long does it take to contact every person on your list?
The average cost of a data breach in 2020 was $3.86 million, according to a new report from IBM and the Ponemon Institute. – Dan Swinhoe, CSO Online
Regardless of where you identify a data breach on the Cyber Kill Chain or MITRE ATT&CK frameworks, internal notification and incident response are crucial, as every second counts.
Communication Process
Manual processes can be the single point of failure in our ever-evolving automated world. Passive communication channels, like email, leave the sender wondering if the recipient has received and read said email. This assumes that a person is sending an email alert. Today many security appliances and platforms are configured to send emails to static email addresses. In most instances, these appliances and platforms are outbound only with no way of confirming delivery or read receipts.
The proliferation of instant messaging applications allows us to look at our screen and see those three dots scrolling which in turn tells our brain the message has been delivered, read, and is being responded to, in real-time. It is this type of technology that continues to transform the digital workplace forcing companies to find solutions that allow us to “work as we live”.
Justine Phillips is a partner with Sheppard Mullin specializing in Privacy and Cybersecurity and a thought leader in Data Breach response, offered some insight into some of the challenges organizations face when responding to data breaches, and other cybersecurity events.
Automation and real-time alert routing saves valuable time to contain and remediate a cyber event. It also gets the right people engaged at the right time to begin the forensic investigation. Many laws impose time-sensitive deadlines and the clock starts running when the event is discovered. – Justine Phillips

Alert Routing Process
Spending on cybersecurity prevention, detection, and incident response has increased exponentially over the last decade, and that trend continues. As good as many of these products are, the number one notification channel continues to be electronic mail. E-mail is a passive way of communication, with the sender often having no idea if the email was received, let alone read. Forget about people changing email addresses or leaving organizations, once an email address has been entered into an appliance or platform it is often forgotten. If your sentry sends up a signal and nobody sees it, then your incident response will be delayed or worse.
To bridge this gap, we should look at automation and alert routing platforms. An alert routing platform should have the ability to tie in your monitoring systems along with your preferred channel of communication: Voice, SMS, Push, Instant Messaging, and yes, even email. For instance, PagerTree allows you to take a single email address and transform it from a serial communication channel into a powerful multi-channel mechanism that triggers multiple communications to multiple people across many channels. In addition to multi-channel communications, PagerTree requires users to actively accept or reject a notification. This allows incident commanders to know, in real-time, who has acknowledged or rejected a given alert notification.
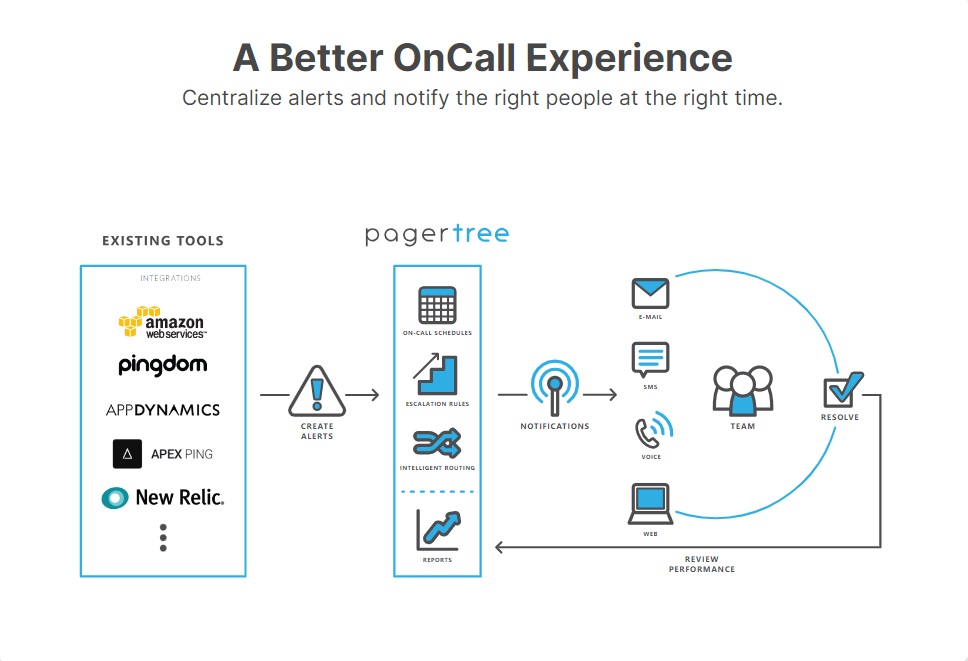
Regardless of your chosen alert routing platform, you should be looking for some of the following characteristics:
- Configuration options that give you the ability to customize how you reach your team: Voice Call, SMS, Push Notification, Instant Messaging, Email
- Easy to use scheduling calendars for one or many team/members
- Configure how often a communication channel is repeated
- Configure how long to try reaching a team member before moving on to the next person on the schedule
- Utilize escalation layers in the event a team member is unavailable
- Alerts initiated via email, webhooks, or other custom integrations
- Redundant telecommunication channels
- Key Performance Indicators (KPI) like Meantime to Respond
- API and other integration opportunities
Ultimately, your alert routing platform should provide you with the confidence to move on to the next steps in your incident response playbook and not focus on who has and has not been alerted. This will allow you to focus your team’s efforts on mitigating the data breach or cybersecurity event, mere seconds after the notification process is initiated, saving you time, frustration, and money.
If you are still searching for an intelligent, alert routing platform, check out PagerTree.If you are still searching for an intelligent, alert routing platform, check out PagerTree. Click here to start a fully functional risk-free trial that could help your organization if it faces a data breach.
